ILOVEYOU
It is the computer worm that attacked more than ten millions of Windows personal computers. The virus started to spread as an email message which includes a subject line “ILOVEYOU” and has the attachment of “LOVE-LETTER-FOR-YOU.txt.vbs.” Once clicked, it had the capabilities of forwarding itself to everybody in the victim’s address book and proceed to overwrite files with itself which makes the computer unbootable. This virus was created by two Filipino Programers, Reonel Ramones, and Onel de Guzman. Yankee Doodle
Yankee Doodle
Yankee Doodle was first discovered in the year 1989, and a Bulgarian hacker created it. It is said when Yankee Doodle was executed, the virus itself becomes the memory resident. Yankee Doodle infects all .com and .exe files. The virus would play a tune “Yankee Doodle” itself every day at 4 PM if it was in memory.
Nimda
Nimda was first found on September 18, 2001. The name of the virus is derived from the word “Admin” if spelled backward. Nimda used Emails, server vulnerabilities, shared folders and file transfer to spread itself. It became the internet’s most widespread virus within 22 minutes. The primary purpose of the virus was to slow down the internet traffic considerable causing a DoS attack.
Morris Worm
In the year 1988 Robert Tappan Morris, the graduate student of Cornell University released the virus which affected approximately 10% of all the computers that were being connected to the internet. At that time 60,000 computers were attached to the internet, and the worm infected 10% of them. The virus had the capability to slow down the computer up to the least point at which it becomes unusable.
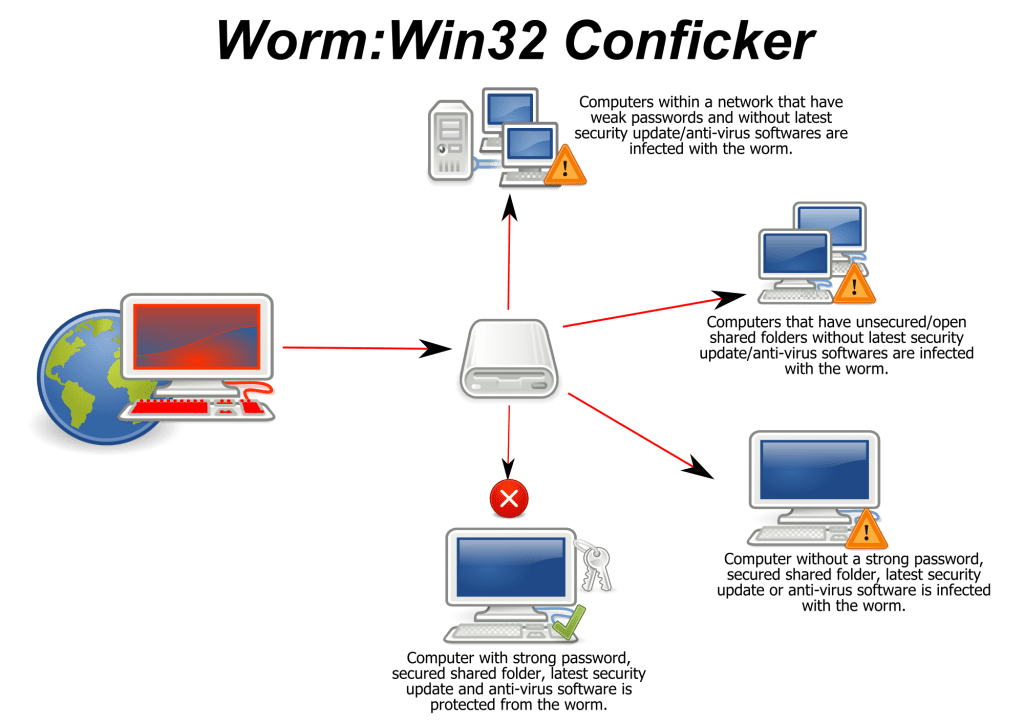
Conficker
Conficker which is also known as Downup, Downadup, and Kido is a type of computer virus that usually targets Microsoft Windows Operating system. The virus was first identified in November 2008. This virus uses flaws of Windows operating system to fetch the administrator password via dictionary attacks while forming a botnet. This virus infected millions of computers which include government, business and home computer in over 190 countries.
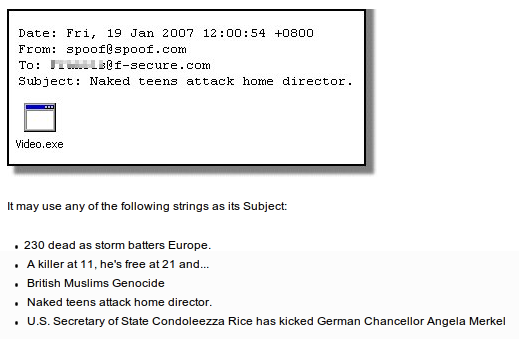
Storm Worm
The Storm Worm is a backdoor trojan horse that was identified in late 2006. Storm worm came in the spotlight when users started receiving e-mails with a subject line about a recent weather disaster “230 dead as storm batters Europe”. The Storm Worm virus easily tricks the victims to click on the fake links that were already infected by the virus turning any Windows computer into a botnet. As of January 22, 2007, the Storm Worm accounted for 8% of all malware infections globally.
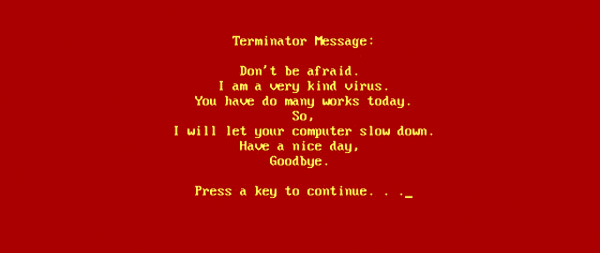
SkyNet
We all know about the Terminator, Skynet is a virus that was inspired by The Terminator movie. It is a very kind virus which makes the victims PC slow very kindly as well as it turns the computer screen red and states “Don’t be afraid. I am a very kind virus. You have done many works today. So, I will let your computer slow down. Have a nice day, Goodbye. Press a key to continue”. This virus infects all .exe files on the computer.
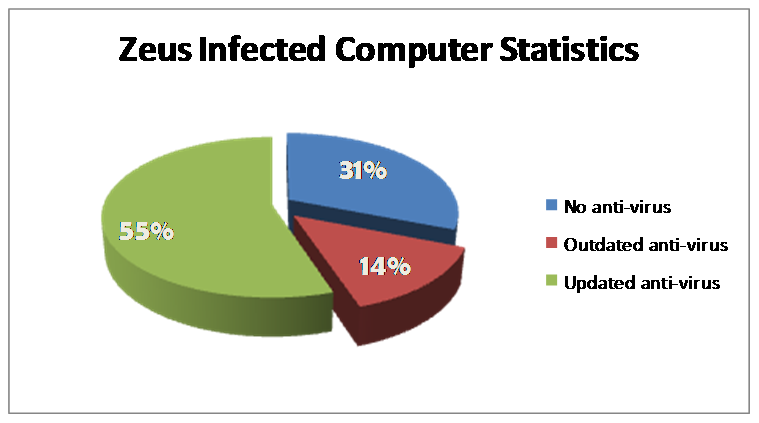
Zeus
This is a type of Trojan horse malware that spreads mainly through drive-by downloads and phishing schemes. It was first recognized in July 2007 when it was mainly used to steal information from the United States Department of Transportation. Zeus virus is very tough to detect because it uses some special stealth techniques that make difficult for an updated antivirus to detect it. Due to its special stealth technologies, this malware has become the largest botnet on the Internet.
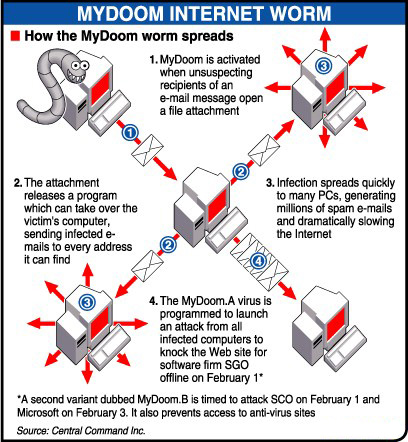
Mydoom
On 1st February 2004, approximately one million computers were infected with Mydoom’s denial of service attacks, and it was the largest such attack to the date. Mydoom virus spread through email which contains the text message “andy; I’m just doing my job, nothing personal, sorry.” When the victim opens the mail the malicious code automatically downloaded and then steal the victim’s whole contacts of email. From where it spread to the victim’s friend, relatives, and colleagues.
SQL Slammer
SQL Slammer is the fast-spreading computer worm that infected most of its 75,000 victims within ten minutes. SQL Slammer dramatically slowed down general Internet traffic and brought down South Korea’s online capacity on knees for 12 hours. SQL Slammer mainly targeted on the servers by generating random IP addresses and discharging the worm to those IP addresses.
Code Red
This virus was initially released on July 13, 2001. However, it affected almost 359,000 computers by July 19, 2001. It was one of the biggest vulnerability at that time the virus was detected and researched by eEye Digital Security employees. According To Symantec “The CodeRed Worm affects Microsoft Index Server 2.0 and the Windows 2000 Indexing service on computers running Microsoft Windows NT 4.0 and Windows 2000, which run IIS 4.0 and 5.0 Web servers. The worm uses a known buffer overflow vulnerability contained in the Idq.dll file.”
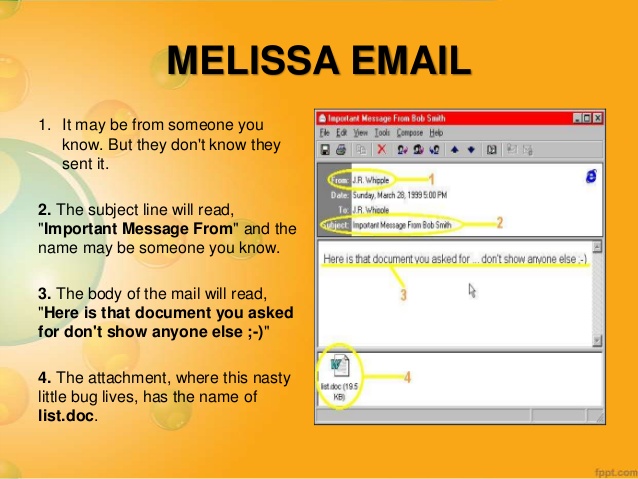
Melissa
Well, this is a virus based on a Microsoft Word macro created by David L. Smith. This virus had an ability to spread itself through email messages. According to the creator, the virus had been named after an exotic dancer from Florida. If victims download this virus via email, this can spread itself to first 50 individuals in an email list.
Sasser
This virus attacks the security controller Local Security Authority Subsystem Service as it had a buffer overflow vulnerability. This targets mostly Windows OS and can prove very dangerous to critical infrastructure. This virus almost caused billions of dollars of damage in the year 2004.
Stuxnet
Well, if you just thought that virus mentioned above are most critical then let me tell you, Stuxnet was found to have shut down one-fifth of the centrifuges in Iranian nuclear power plants. This virus was first identified in the year 2010 and targets mostly industrial computer system.
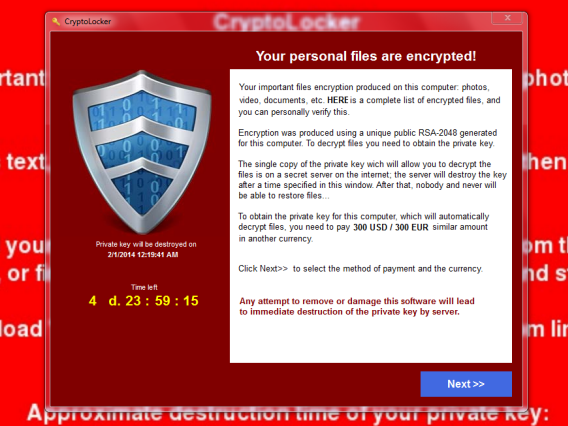
Cryptolocker
Well, it’s a ransomware Trojan that spreads via email attachments. It almost has been compromised nearly 500,000 computers and encrypted its files until the ransom amount has been paid. According to the reports from Rantnow, “The leader of the group behind Cryptolocker, Evgeniy Bogachev, was eventually caught with the total cost of his crimes equaling 3 million dollars.”
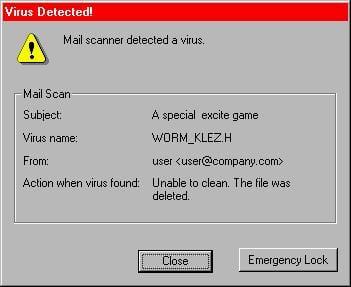
The Klez Virus
Klez Virus makes its way to the digital world in late 2001. This virus infects victim’s computer through an e-mail message, replicated itself and then sent itself to people in the email address book. On further testing, it’s found that the Klez Virus act as a normal virus. However, this virus is capable to disable the antivirus system that’s installed on victim’s computer. Hackers later modified the Klez virus to make it more effective. The virus was programmed to spam people with multiple e-mails that clog an inbox in short order.
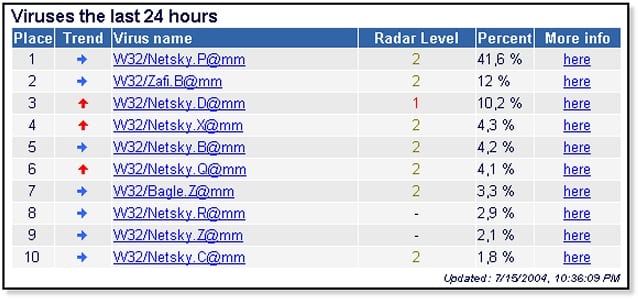
Netsky Virus
Well, this virus spread itself through e-mails and Windows networks. The Netsky virus spoofs e-mail addresses and propagates through a 22,016-byte file attachment. After spreading itself, it can cause DoS (Denial of Service) attack. After doing the attack system collapse while trying to handle the amount of internet traffic.
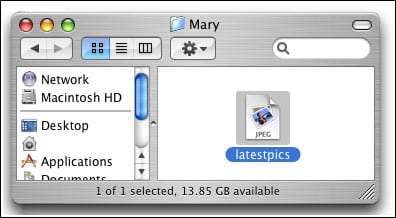
Leap-A
Leap-A which is also known as Oompa-A debuted in the year 2006. Leap-A virus targeted Mac systems and it used the iChat instant messaging app to propagate across vulnerable Mac Computers. After infecting the Mac computer, the virus spread itself to all iChat contacts and sends a message to each and every person. The message that the virus sents contains a corrupted file that looks like a JPEG image. That corrupted file destroyed many Mac Computer and this is where Leap-A became popular.
Slammer
Well, this is a type of virus we often see in movies related to technology. Well, this virus is a great example of ‘Denial of Service’ attack. The virus is powerful enough to bring down an entire system. The severity of Slammer is evident from reports of some of the worst breakdowns ever seen: 911 emergency services being down, the Bank of America’s ATM network crashed and more.
Pikachu
Well, at the year 2000, the first computer virus targeting children was released, known as Pikachu Virus. The virus was designed as an actual email that included the Pokemon character, Pikachu. The email carried an image of the Pokemon, but with that imaged unsuspecting children released a Visual Basic 6 program called pikachupokemon.exe that removed the contents of directories. Even if you are not a computer expert, you can protect yourself from viruses and worms before they reach your machine. Here are some tips that you can follow:
Keep an updated antivirus software installed and scan your computer Do not open e-mails from external sources, don’t open spammy links. Allow Windows to update, and many time windows updates bring some security updates that could fix the existing flaws from your computer Don’t download software from unreliable sources.